What is Incident Management?
According to ITIL (Information Technology Infrastructure Library), incident management deals with any “unplanned disruption to an IT service or reduction in the quality of an IT service”. The aim of incident management is to restore the normal operation of IT services as quickly as possible in order to minimize financial losses and service outages and thus ensure customer satisfaction.
Incident Management, or IT Incident Management, is thus a process within IT Service Management (ITSM) that focuses on the rapid identification, prioritization, investigation and resolution of incidents that affect normal IT operations. The tool helps to quickly identify the affected systems and components and understand the extent of the incident.
Malfunctions or incidents can be caused by human or technical failure, security breaches or various other events. In the incident management process, IT support identifies incidents and prioritizes them accordingly in order to provide a quick solution.
At a higher level, incident management is an important component of IT service management and aims to maintain IT service levels and ensure IT service availability for the company. It is crucial for guaranteeing service level agreements (SLAs) and therefore also for customer and user satisfaction.
In summary, incident management is an important process within ITSM according to ITIL that focuses on the rapid identification and resolution of incidents in order to restore normal IT operations as quickly as possible and minimize damage to the company.
Good to know: In the narrower sense, IT Incident Management can therefore take into account organizational as well as detailed legal and technical issues.
What is an IT incident? Definition according to ITIL
But what exactly are incidents? According to ITIL, an “incident” is “an unplanned interruption to a service or a reduction in the quality of a service.”
According to this description, the term “incident” can be defined very broadly – from a deterioration in network quality to a lack of storage space to a cyber attack that threatens the entire IT security. The detection of such security-relevant incidents and the response to them is referred to as security incident management or incident response management. We discuss this specific case in more detail below under “The incident response lifecycle”.
Incidents can have many negative effects on day-to-day operations. They cause longer downtimes and can also result in significant data loss. It is therefore essential to have a good incident management system in place, as disruptions and failures within IT are unfortunately unavoidable. However, it is possible to plan how to deal with this.
Types of incidents that may occur in companies
Typical incidents can include a variety of errors, such as network connectivity issues, hardware failures, application deviations, system failures, software errors or security breaches, etc.
Companies operating in regulated industries such as healthcare or financial services may need to meet compliance requirements (for example NIS2) when dealing with incident management.
In the Service Management area, on the other hand, it is important that Incident Management processes are clearly defined and well documented to ensure that service levels are met and customers are satisfied.
However, there are also incidents that are not attributable to IT equipment or software. For example, problems with access systems or permissions can trigger incidents. Disrupted processes can also lead to incidents that not only affect technical devices, but also describe problems with responsibilities or organizational rules.
This extends the definition of incidents to include company processes. This is related to change processes in the company, which are supported by so-called changes.
Some possible specific topics that can be addressed in the context of incident management in different industries or specialties are:
Depending on the challenges an organization has in its specific area, certain incident management aspects may be more important than others, and it is important to focus on the issues that are relevant to your needs.
What is the difference between Problem and Incident Management?
Problem Management is the process of identifying and eliminating underlying causes to prevent recurring problems. The aim of incident management, on the other hand, is to quickly restore normal operations. A problem is therefore the cause of one or more malfunctions.
The Importance of Incident Management
The importance of Incident Management for companies is enormous. IT system failures can be protracted and harm companies in many ways – not only financially. In addition to the potential loss of revenue and poorer customer relations, an IT outage also impacts productivity, work efficiency and employee satisfaction.
In short, intelligent incident management offers these advantages:
What makes Incident Management so efficient?
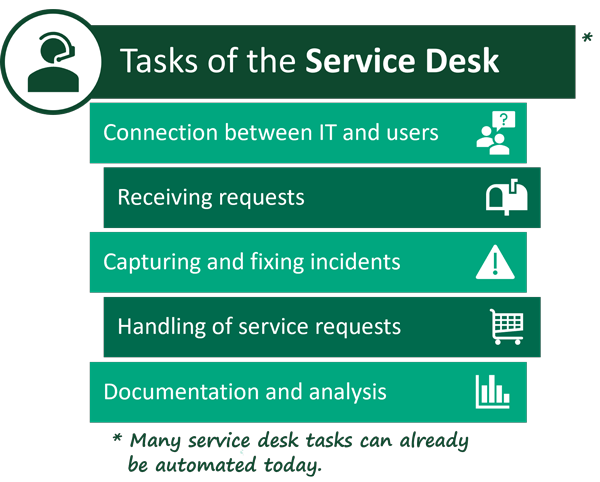
Incidents are documented in form of tickets. Tickets are handled and monitored by a service desk. The tasks of a Service Desk team therefore include both the fast and goal-oriented receipt of service requests and the qualification of requests, which can include faults, problems, tickets and incidents.
This structured approach makes it easier for IT staff to respond quickly to problems that arise and provide solutions efficiently, which in turn leads to smoother operations and increased customer satisfaction. By systematically recording and processing incidents, incident management ensures efficient problem handling in the IT area.
Good incident management tools, such as those from REALTECH, often offer a range of functions to automate repetitive tasks and thus speed up the process. Automation also gives you the opportunity to standardize your processes. This enables you to follow guidelines and procedures, which in turn can contribute to meeting compliance requirements.
You can also use our Incident Management Tool to analyze trends and patterns to identify potential incidents early and proactively handle them. By analysing incident data, you can identify patterns that indicate recurring problems, which can prevent or minimize future disruptions.
REALTECH Incident Management is even appreciated by end users. The tool offers simple ticketing in familiar environments such as MS Teams and SAP. These integrations allow users to create tickets quickly and easily without having to access the actual service desk portal.
The role of AI in Incident Management
The increasing popularity of artificial intelligence (AI) has revolutionized the efficiency of various business processes, including incident management. AI technologies play a crucial role in resolving incidents by providing automated solutions for effective ticket handling.
Artificial intelligence automates the categorization and routing of tickets by using Natural Language Processing (NLP) and Machine Learning (ML) to understand and act on incoming requests. By analyzing content, it identifies relevant keywords, patterns and contexts to effectively categorize, prioritize and assign tickets to the right supporters.
AI-based systems continue to support the incident solution by providing contextual information and automated solution suggestions. They access knowledge databases to find proven solutions and offer suitable knowledge articles. This speeds up the resolution process and ultimately improves service quality and user satisfaction.
The Incident Response Lifecycle
Security incidents require rapid intervention, where threats or events are detected, analyzed and resolved in real time. Here, companies use specific methods and tools consisting of a combination of IT automation and human expertise. The aim is to keep damage to a minimum and prevent any incidents.
Operators of critical infrastructures in particular must prove that their information security measures meet the legal requirements for risk management:
- All incidents must be documented seamlessly.
- Solution scenarios for security incidents must be predefined and quickly retrievable.
- Responsibilities must be clarified and processes (workflows) must be adhered to.
What is a Security Incident and how is it triggered and resolved?
Security Incident Response is a similar process to incident management, but is applied specifically to security incidents. A security incident can be of many different types – for example, it can be an active threat or a breach of data protection guidelines. These incidents can occur both inside and outside a company.
Incident response is the process of responding to IT threats such as cyber attacks, security breaches and server failures. Since these security-threatening incidents are accompanied by serious consequences that are not necessarily only financial, it is important to be particularly vigilant. This is why a detailed framework for resolving such incidents has been developed: the incident response lifecycle.
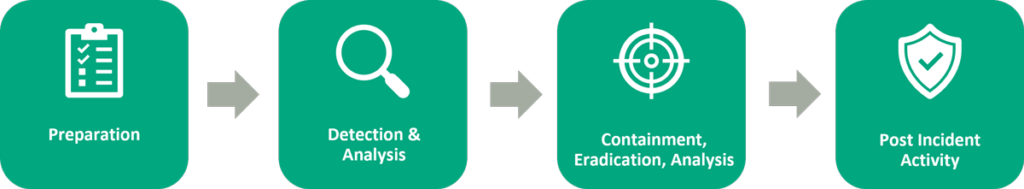
In theory, various approaches have been established for this purpose and one of the best known is the Incident Response Lifecycle according to the National Institute of Standards and Technology (NIST). This divides incident response into four main phases:
- Preparation
- Detection and analysis
- Containment, elimination and restoration
- Activities after the event
Phase 1: Preparation
The preparation phase comprises the measures that a company takes to prepare for the incident response. These include, for example, setting up the right tools and training the team. This phase includes activities aimed at preventing incidents.
Phase 2: Recognize and analyze
Accurate incident detection and assessment is often the most difficult aspect of incident response for many organizations, according to NIST. In principle, a problem can arise in any project phase and can be internal in nature or related to suppliers or your customers. This may affect the incident’s prioritization that you make later in the process. Always capture the following information when identifying a fault:
- Name or ID number
- Description
- Date
- Incident Manager
This information will serve as your reference later, especially if you are working with a Problem Management plan. It also allows you to identify the root cause of the fault (problem management) and ensure that it does not occur again.
In order to be able to react appropriately to a malfunction, an analysis is required to determine the malfunction and prioritize it in the workflow. Only then can the solution phase begin. For most malfunctions, there is a predefined solution path.
However, if this person is not directly available, it may be necessary to forward the problem to be resolved with the help of the appropriate department heads. In such a case, a creative approach to the problem and temporary solutions may be necessary.
Phase 3: Containment, removal and recovery
Once you have analyzed the malfunction and found the cause, it is time to delegate the tasks of your response plan. You do this by assigning resources. The best way to do this is in an incident log or with the help of work management software.
Regardless of what you decide to do: All involved and, if applicable, relevant persons should be informed about the action plan. This ensures a good overview, open communication and therefore efficient incident management.
This phase focuses on minimizing the impact of the incident and mitigating service disruptions. At this stage, you also need to make sure that all the measures in your response plan actually produce the desired results before you complete any outstanding tasks.
Whether you work with a ticket system, a service desk, or service requests: It’s reassuring to know that there are no more unresolved to-dos. As soon as all tasks have been completed, you can officially finalize the response plan with a clear conscience and move on to documenting the incident.
For companies dealing with critical infrastructures, response plans, clear responsibilities and comprehensive documentation using a ticket system are important and possibly even indispensable tools for successfully passing an audit.
Phase 4: Post-incident activities
One of the most important parts of incident response that is often forgotten is that you learn from it and improve. The final phase in the Incident Management process is therefore the final documentation of the results of your response to the problem. You should save all the information you have collected in the previous steps in a shared workspace so that you can easily access it in the future.
In this phase, the incident itself and the incident response efforts are analyzed. The aim is to limit the likelihood of the incident occurring again and to identify opportunities to improve future incident response activities.
Overall, the concept of these four phases is based on a sound knowledge base. The effectiveness of phase three is highly dependent on the success of phases one and two. If Incident Management is to provide optimal protection and you want to ensure the recovery of IT services in the enterprise, all four phases must be implemented successfully.
7 Tips for efficient Incident Management
Once you know how to proceed in the event of an incident, you can start to create a customized incident log that fits your company’s requirements. In any case, the most important methods in Incident Management include well-organized and clear logging, training for the team, effective communication within the team and, wherever possible, automating processes.
Getting started can be quite challenging, which is why we are giving you 7 tips here so that you can document faults correctly and rectify them accordingly.
Conclusion: Incident management is essential
With the growing complexity of IT, its service offerings, service structures and the increasing number and sophistication of threats, organizations are facing unprecedented risk. With effective Incident Management, you can mitigate this risk by identifying and resolving incidents faster.
While outages and other incidents are unavoidable for any business, incident management is the most effective way to initiate an immediate response and prevent costly downtime that can harm your organization’s reputation and business performance.